Advanced Installation and Configuration
Everything you need to install and configure SOARCA
After completing the Getting Started setup for SOARCA, you may find that certain advanced configurations or customizations are necessary to optimize SOARCA for your specific use cases, for example integrating with The Hive. This section provides in-depth guidance on additional steps you can take to enhance, secure, and integrate SOARCA with your infrastructure, ensuring it meets your unique operational needs.
Configuring SOARCA
| Variable | Content | Description |
|---|
| PORT | 8080 | Set the exposed port of SOARCA. Default is 8080. |
| ENABLE_TLS | false | Enable TLS for secure communication. Default is false. |
| CERT_FILE | "/certs/server.crt" | Path to the TLS certificate file. Default is "/certs/server.crt". |
| CERT_KEY_FILE | "/certs/server.key" | Path to the TLS certificate key file. Default is "/certs/server.key". |
| MAX_EXECUTIONS | 1000 | The number of historical executions saved, including the current one. Default is 1000. |
| SOARCA_ALLOWED_ORIGINS | * | Set allowed origins for cross-origin requests. Default is *. |
| GIN_MODE | release | Set the GIN mode. Default is release. |
| DATABASE | false | Set if you want to run with an external database. Default is false. |
| MONGODB_URI | mongodb://localhost:27017 | Set the MongoDB URI. Default is mongodb://localhost:27017. |
| DATABASE_NAME | soarca | Set the MongoDB database name when using Docker. Default is soarca. |
| DB_USERNAME | root | Set the MongoDB database user when using Docker. Default is root. |
| DB_PASSWORD | rootpassword | Set the MongoDB database user password when using Docker. Change this in production! Default is rootpassword. |
| PLAYBOOK_API_LOG_LEVEL | trace | Set the log level for the playbook API. Default is trace. |
| MAX_REPORTERS | 5 | Set the maximum number of downstream reporters. Default is 5. |
| LOG_GLOBAL_LEVEL | info | One of the specified log levels. Default is info. |
| LOG_MODE | development | Set the logging mode. If production, LOG_GLOBAL_LEVEL is used for all modules. Default is development. |
| LOG_FILE_PATH | "" | Path to the logfile for all logging. Default is "" (empty string). |
| LOG_FORMAT | json | Set the logging format. Either text or json. Default is json. |
| ENABLE_FINS | false | Enable FINS in SOARCA. Default is false. |
| MQTT_BROKER | localhost | The broker address for SOARCA to connect to for communication with FINS. Default is localhost. |
| MQTT_PORT | 1883 | The port for the MQTT broker. Default is 1883. |
| HTTP_SKIP_CERT_VALIDATION | false | Set whether to skip certificate validation for HTTP connections. Default is false. |
| VALIDATION_SCHEMA_URL | "" | Set a custom validation schema to validate playbooks. Default is "" to use the internal schema. Note: Changing this can heavily impact performance. |
Integrations
The Hive
| Variable | Content | Description |
|---|
| THEHIVE_ACTIVATE | false | Enable integration with The Hive. Default is false. |
| THEHIVE_API_TOKEN | your_token | Set the API token for The Hive integration. |
| THEHIVE_API_BASE_URL | http://your.thehive.instance/api/v1/ | Set the base URL for The Hive API. Default is "". |
Authentication
Note
More information on setting up authentication can be found
here.
| Variable | Content | Description |
|---|
| AUTH_ENABLED | false | Enable authentication. Default is false. |
| OIDC_ISSUER | https://localhost:9443/application/u/test/ | The OIDC issuer URL. |
| OIDC_CLIENT_ID | SOME_CLIENT_ID | Set the OIDC client ID. |
| OIDC_CLIENT_SECRET | SOME_CLIENT_SECRET | Set the OIDC client secret. |
| OIDC_REDIRECT_URL | http://localhost:8081/auth/soarca_gui/callback | Set the OIDC redirect URL. |
| COOKIE_SECRET_KEY | SOME_COOKIE_SECRET | Optional: Secret key for cookies. Generate using openssl rand -base64 32 or `head -c 32 /dev/urandom |
| OIDC_SKIP_TLS_VERIFY | true | Set whether to skip TLS verification. Default is true. |
| AUTH_GROUP | soarca_admin | Specify the group users must belong to for authentication against SOARCA. |
Key management system
Note
More information on the key management system can be found
here.
| Variable | Content | Description |
|---|
| ENABLE_SSH_KMS | false | Enable the key management system for SSH |
| SSH_KMS_DIR | deployments/docker/testing/ssh-kms-test/ssh-keystore/ | Set the folder where SSH keys for the key management system are stored |
1 - Setup RBAC for SOARCA
Setup OIDC based Role-Based Access Control (RBAC) for SOARCA
Authentication is disabled by default in SOARCA. This means that when SOARCA is launched with its default configuration and exposed to a network, anyone can interact with it. Since SOARCA requires significant capabilities and access to reconfigure systems, exposing it without authentication poses a security risk. This section outlines how to set up authentication and authorization for SOARCA.
SOARCA leverages our internally developed gauth library as its underlying authentication framework. This library provides convenient Role-Based Access Control (RBAC) middleware, which manages authentication for various endpoints, such as the Playbook API. Based on OpenID Connect (OIDC), the library supports integration with multiple authentication providers.
Currently, for the used gauth library the Authentik authentication provider, an open-source solution that supports a wide range of authentication methods is supported and tested. As such other OIDC-based providers might not be compatible.
Supported OIDC-Based Auth Providers
Enabling RBAC
Enabling RBAC can be done by setting the AUTH_ENABLED: true.
AUTH_ENABLED: true
AUTH_GROUP: "soarca_admin"
OIDC_ISSUER: "https://authentikuri:9443/application/u/test/"
OIDC_CLIENT_SECRET: "SOME_CLIENT_SECRET"
OIDC_CLIENT_ID: "SOME_CLIENT_ID"
OIDC_SKIP_TLS_VERIFY: true
Setting up Authentik with SOARCA
Next, we need to obtain variables such as OIDC_ISSUER etc. This section will describe how we can setup Authentik.
Spinning up Authentik
Instruction and docker-compose on how to bundle SOARCA with Authentik will come!
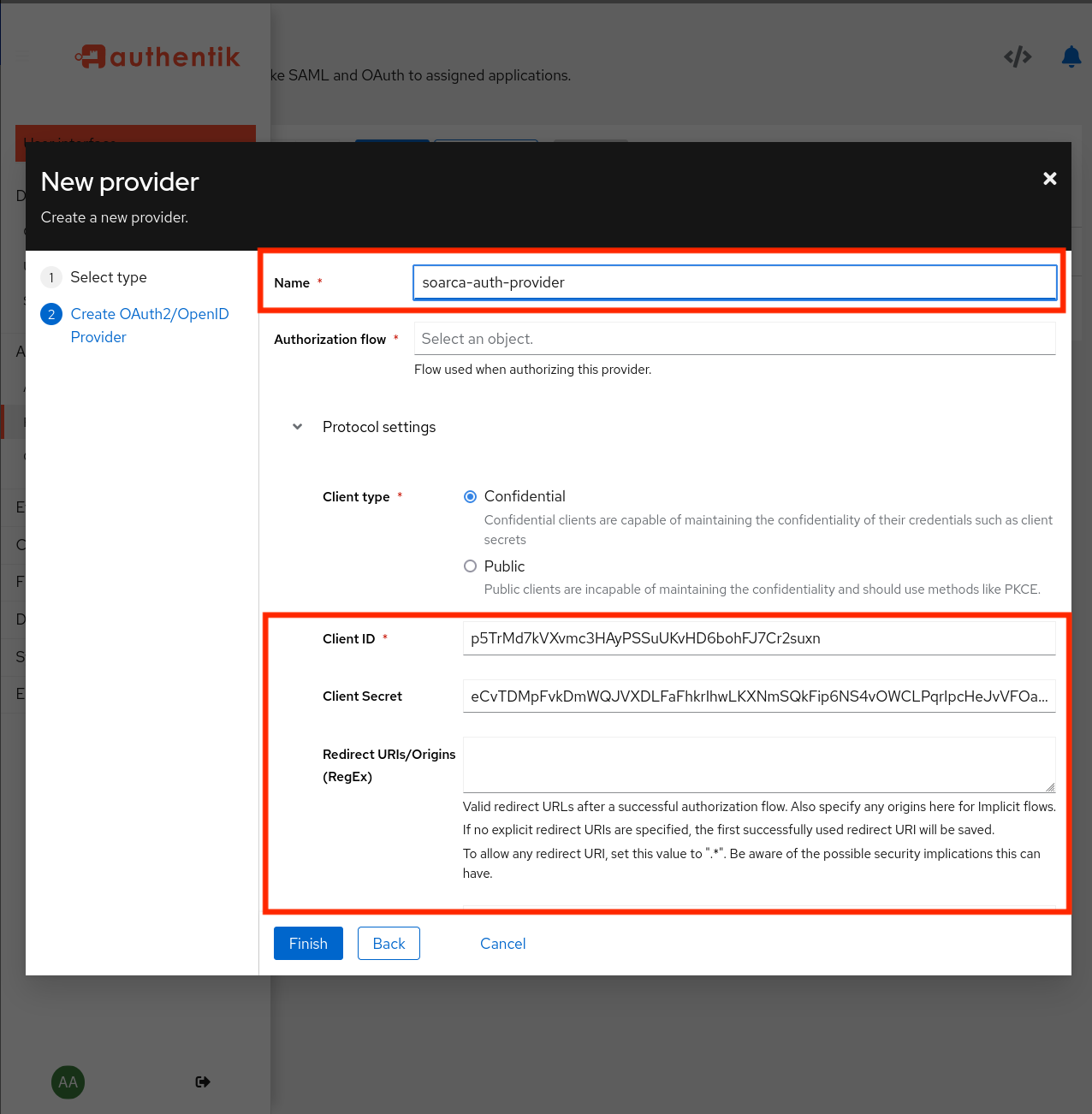
Making an authentication provider
In Authentik first setup a new provider. This can be done under Applications -> Providers ->Create. For the provider type select the OAuth2/OpenID provider from the various options. An example configuration is given below:
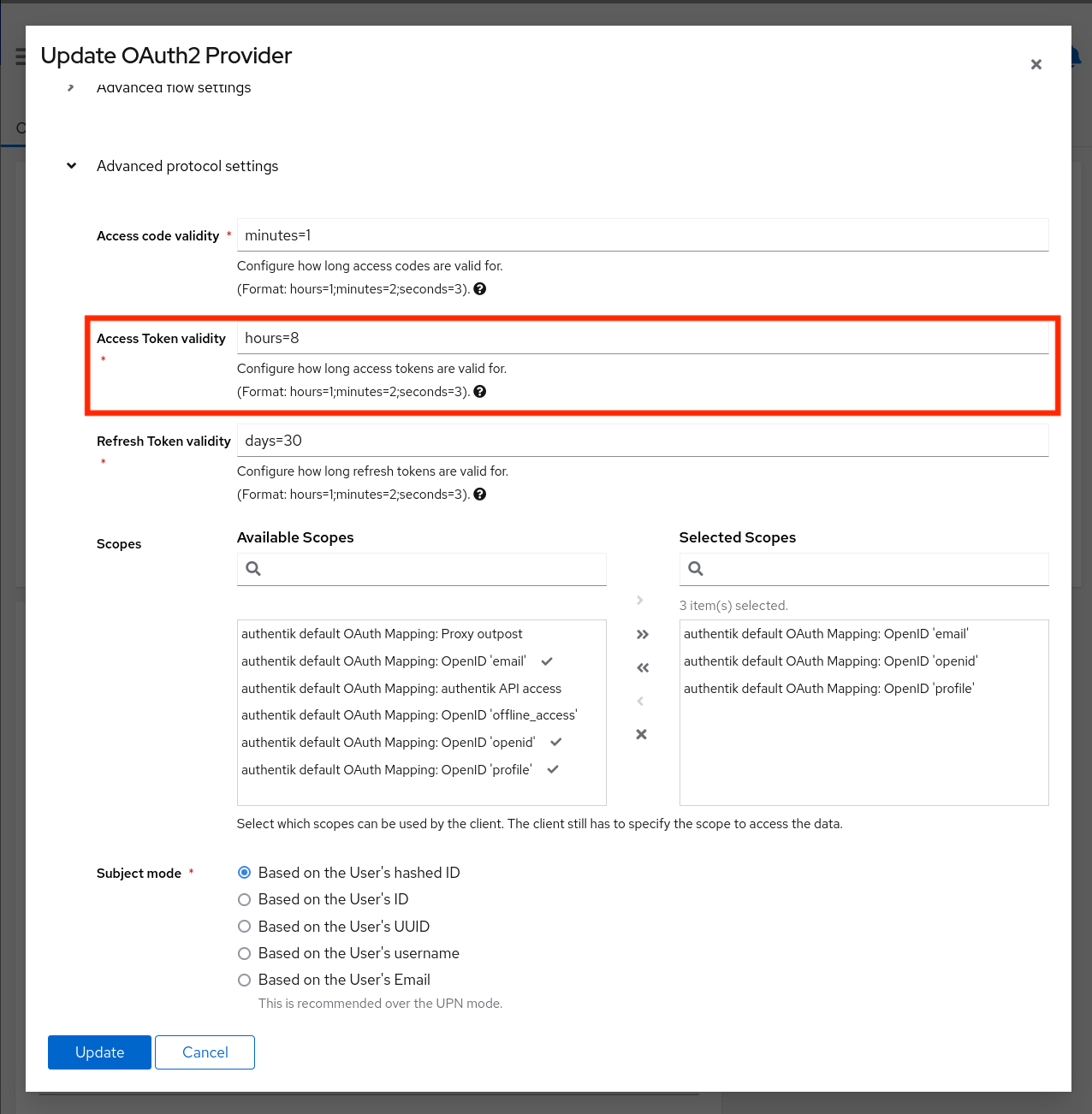
Note
We use an token lifetime of
8 hours, since the
SOARCA-GUI uses this token for client validation. As we do not want the user to login every so minute. It is advised to set this to 8 hours.
Next, we need to set in the advanced protocol settings the token expiration lifetime needs to be changed to 8 hours.
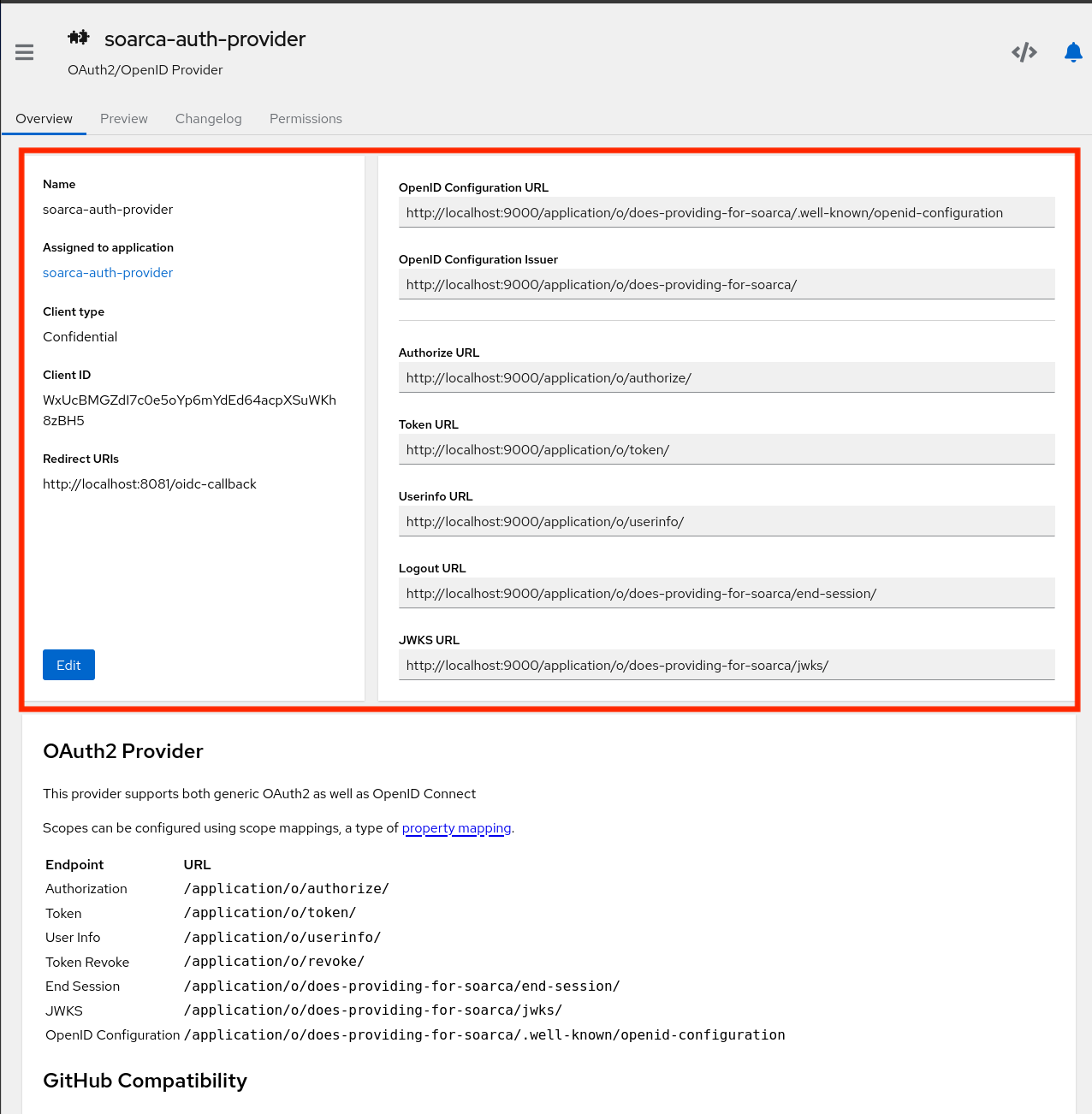
Endpoints for the auth provider can also be found here:
Making an application
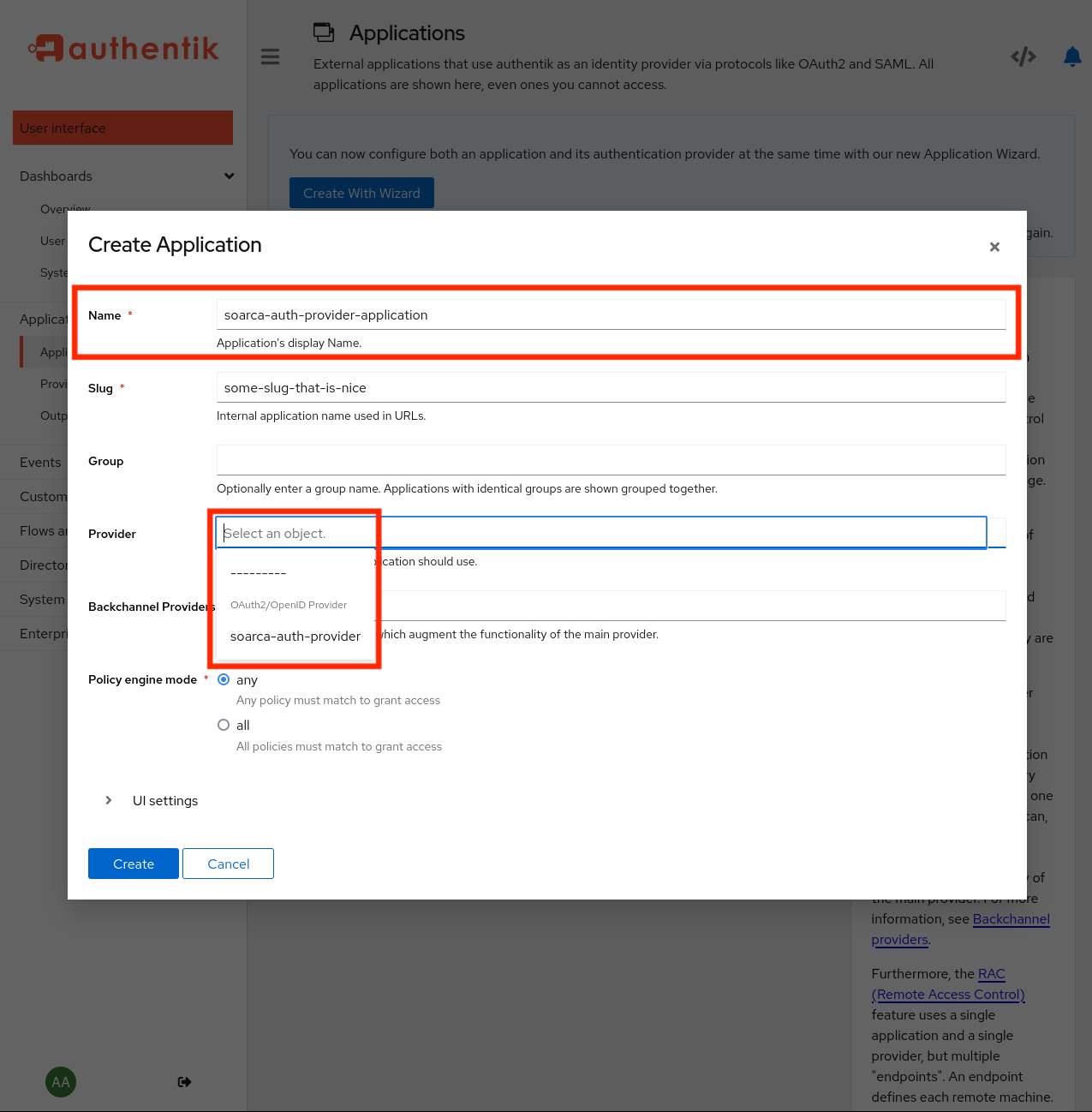
Next, we can create a new application as shown in the picture below. A new application can be added under Applications –> Create Add the earlier made provider to this application.
Setting the authentication provider
Next, under providers -> soarca-auth-provider -> edit we can find the following overview:
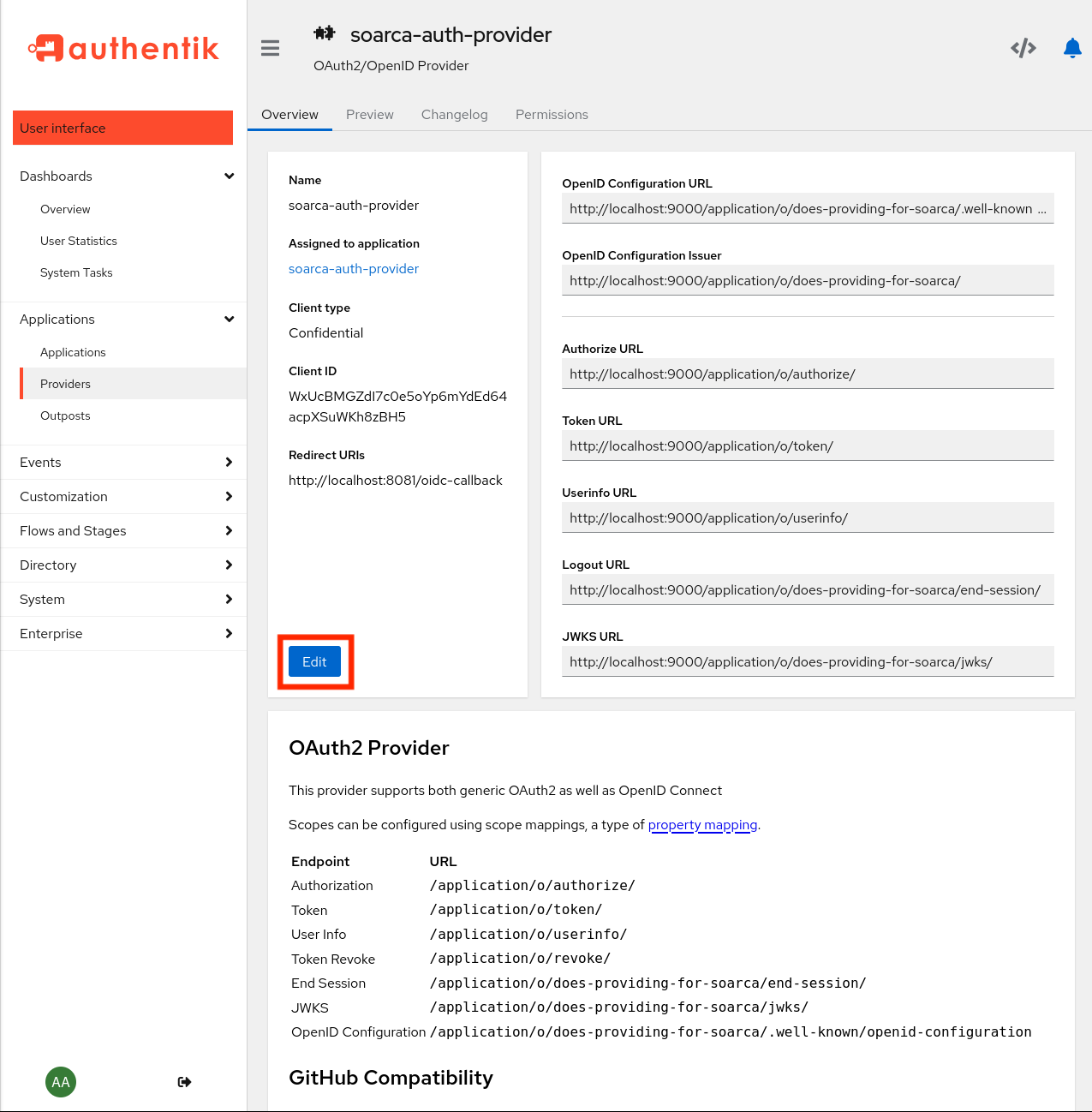
Here we can find the:
- Client ID:
some random stuff - Client Secret:
some other random stuff - Redirect Url: Optional, should be set when using for the SOARCA-GUI explained [here]
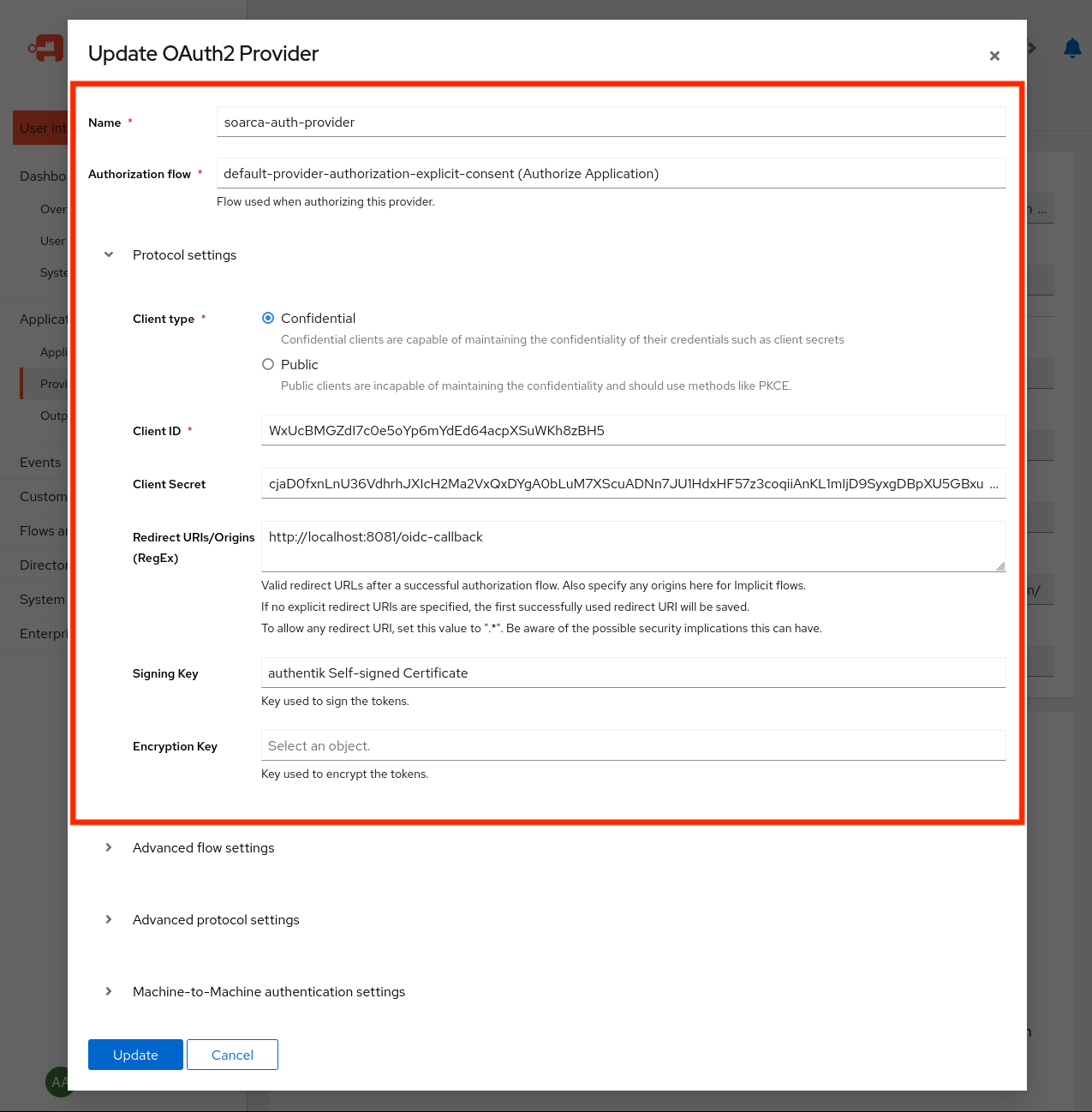
We only use the Authentik integration for token validation on the SOARCA side. As such, only the OIDC_CLIENT_ID is required here. For the SOARCA-GUI, we would need the OIDC_CLIENT_SECRET.
Warning
It is not advised to run Authentik like this! Please setup TLS certificates in a real environment and set the OIDC_SKIP_TLS_VERIFY to false.Set these variables in the environment variables settings, for example:
AUTH_ENABLED: true
AUTH_GROUP: "soarca_admin"
OIDC_ISSUER: "https://authentikuri/application/o/does-providing-for-soarca/"
OIDC_CLIENT_ID: "WxUcBMGZdI7c0e5oYp6mYdEd64acpXSuWKh8zBH5"
OIDC_SKIP_TLS_VERIFY: true
export AUTH_ENABLED=true
export AUTH_GROUP="soarca_admin"
export OIDC_ISSUER="https://authentikuri:9443/application/o/does-providing-for-soarca/"
export OIDC_CLIENT_ID="WxUcBMGZdI7c0e5oYp6mYdEd64acpXSuWKh8zBH5"
export OIDC_SKIP_TLS_VERIFY=true
Adding SOARCA user group and users
Note
Again, for the current version of the implementation we only support one group to differentiate between access to the different endpoint. We plan for a later version of SOARCA to have different groups/permissions for a given API endpoint.For the current version of SOARCA and the gauth library the access to the API for a given user is dependent on the required set AUTH_GROUP. Users are required to be in the same group as the group that has been set through this variable. Currently, there is not yet control over which group can access a specific API or route grooup. This feature is scheduled for a future version of SOARCA. In the example below, the AUTH_GROUP: soarca_admin is set.
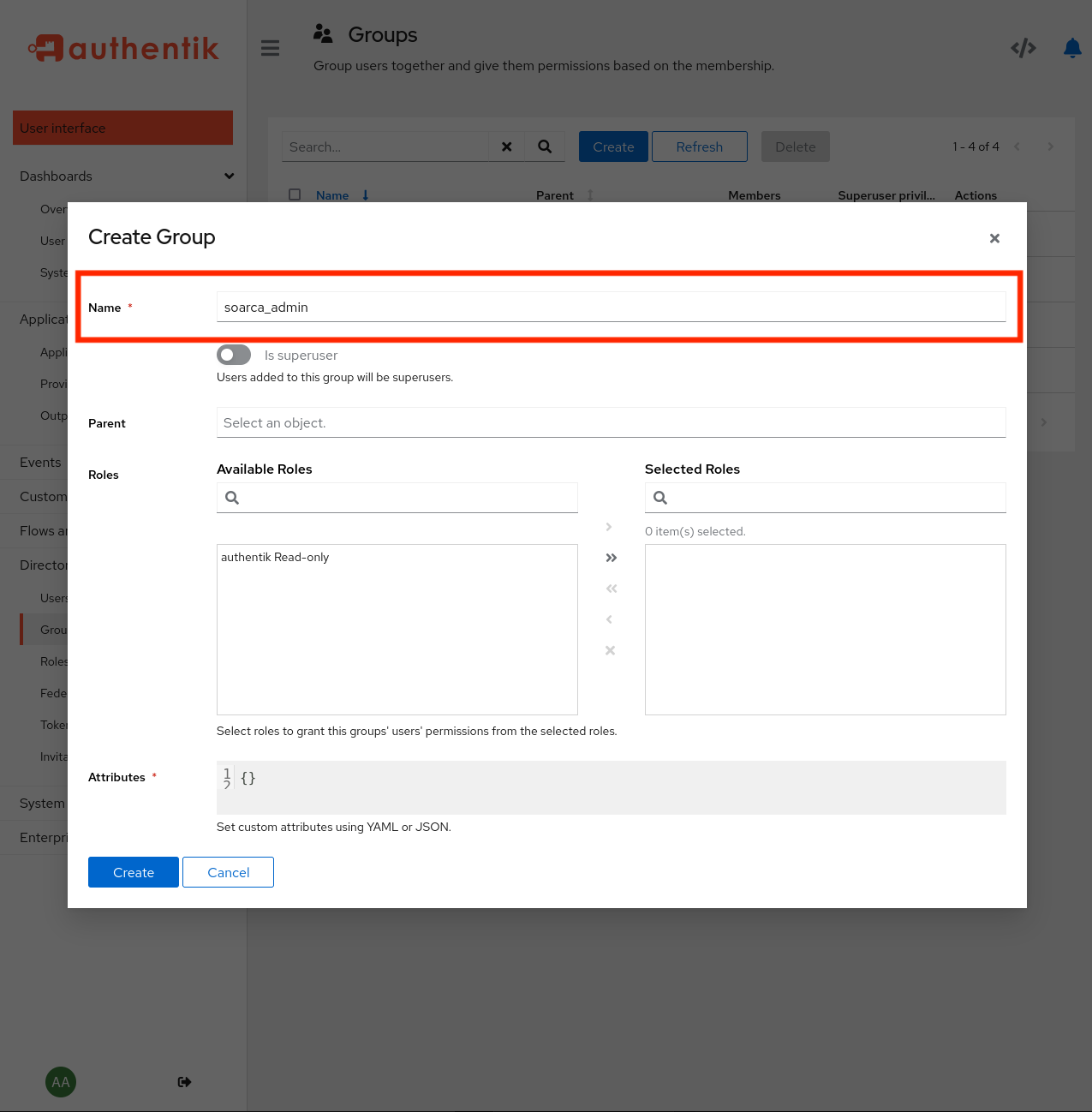
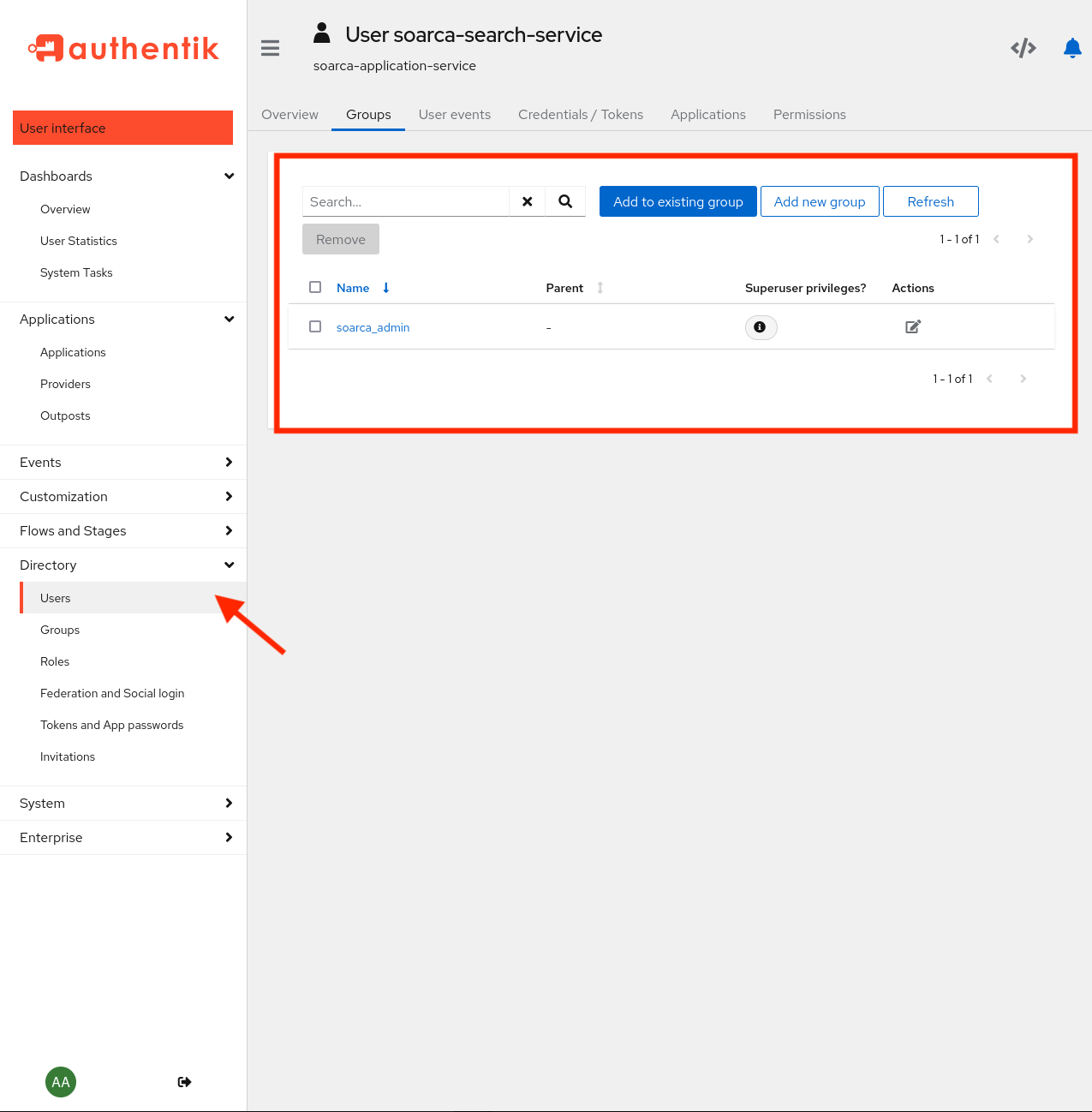
Next, we require to setup a group in Authentik that is called soarca_admin as explained earlier. The to be obtained tokens from Authentik needs to have this group information as this will be checked by the middleware. A group can be created under Directory -> Groups -> New.
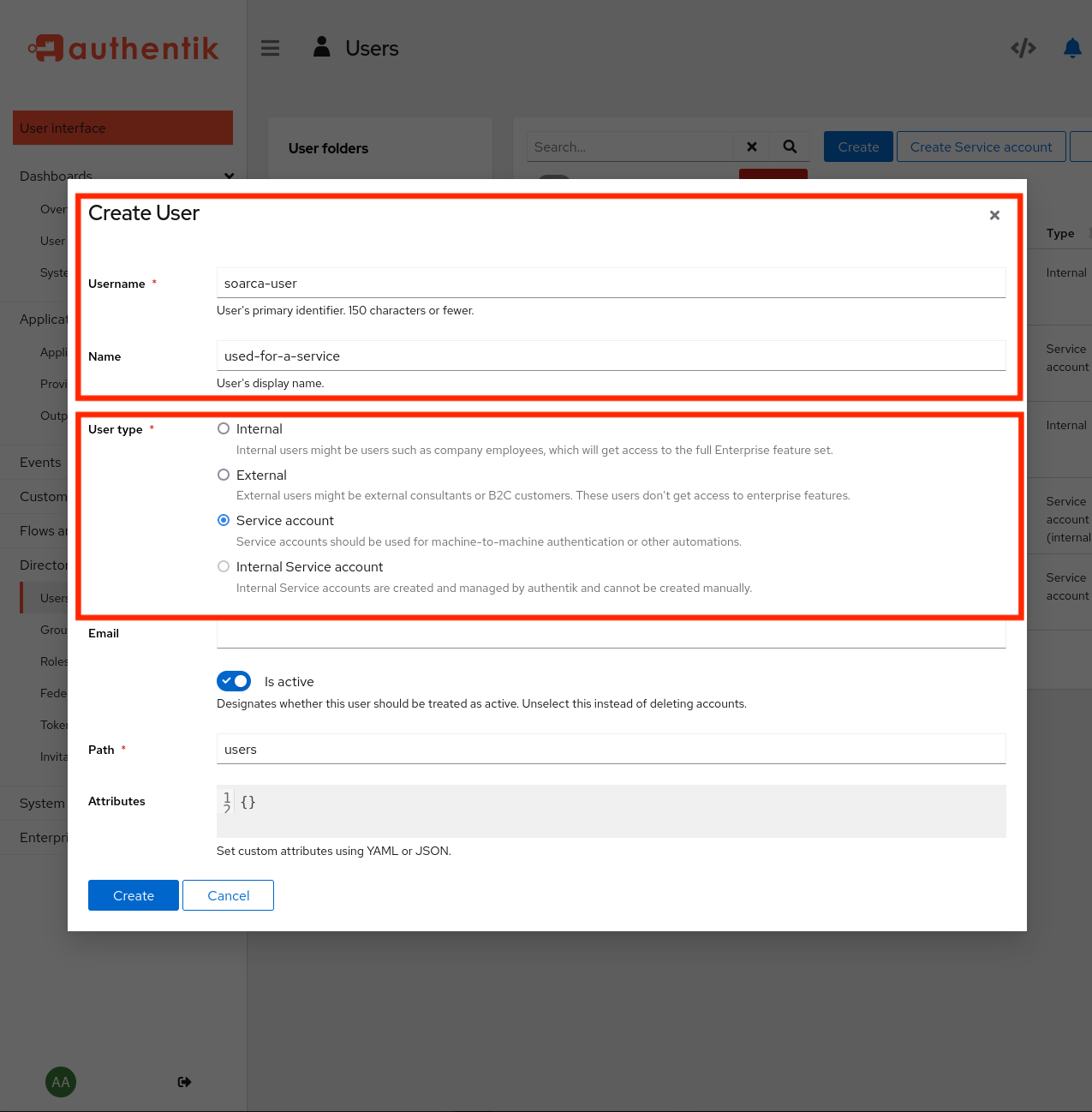
Under users normal as as service accounts can be created. We advise for machine-to-machine implementation service accounts, and for normal users (used for example for SOARCA-GUI logins) normal accounts. Now we can make an users and add to the soarca_admin group. Make use under the application that this group is added to the application provider that we have setup earlier, otherwise the grants of token might fail.
Authentication with Bearer
Now that authentication and authorization is enabled, every request requires to have a set Authorization: Bearer <token> header.
POST /trigger/playbook/ HTTP/1.1
Host: localhost:8080
Content-Type: application/json
Authorization: Bearer <token from authentik>
Content-Length: 2345
{
"type": "playbook",
"spec_version": "cacao-2.0",
"id": "playbook--300270f9-0e64-42c8-93cc-0927edbe3ae7",
"name": "Example ssh",
...
}
The gauth library will validate this bearer token against the setup Authentik provider and grant the user or application access. Replace the token with a working bearer token.
Tip
For obtaining an access (bearer) token for Authentik, we have provided an example
hereAn example curl command is provided below:
curl -X POST -H "Content-Type: application/json" -H "Authorization: Bearer <replace token>" -d @./example/ssh-playbook.json localhost:8080/trigger/playbook








